Id Try This Old Trick Again
When yous hear "security breach," what springs to mind? A malevolent hacker sitting in forepart of screens covered in Matrix-style digital text? Or a basement-dwelling teenager who hasn't seen daylight in iii weeks? How about a powerful supercomputer attempting to hack the entire globe?
Hacking is all near one thing: your password. If someone can guess your password, they don't need fancy hacking techniques and supercomputers. They'll only log in, interim as you lot. If your password is short and simple, it'southward game over.
There are eight common tactics hackers apply to hack your password.
one. Dictionary Hack
First up in the common countersign hacking tactics guide is the dictionary assail. Why is it called a lexicon attack? Because information technology automatically tries every word in a defined "lexicon" against the password. The dictionary isn't strictly the one you lot used in school.
No. This lexicon is actually a small file containing the most commonly used password combinations. That includes 123456, qwerty, password, iloveyou, and the all-time classic, hunter2.
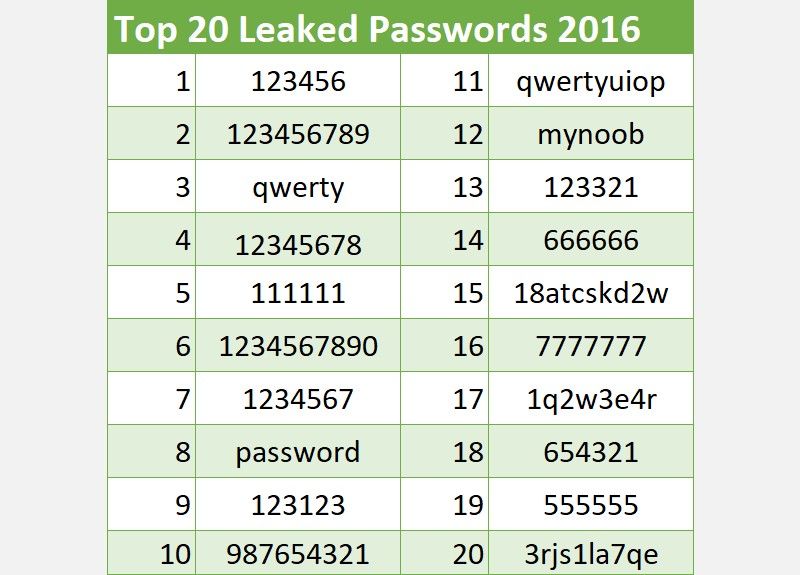
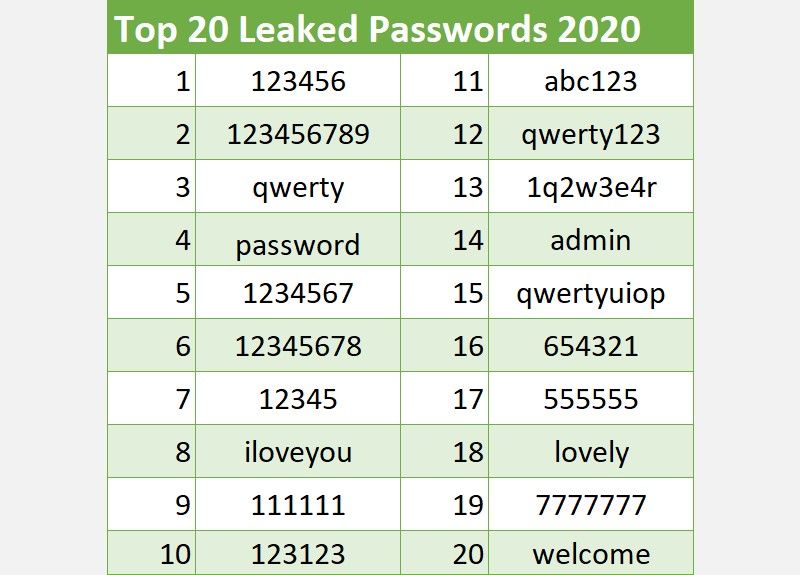
The above table details the nearly leaked passwords in 2016. The below table details the near leaked passwords in 2020.
Annotation the similarities between the two—and brand sure yous don't use these incredibly elementary options.
Pros: Fast; volition normally unlock some woefully protected accounts.
Cons: Even slightly stronger passwords will remain secure.
Stay safe: Use a strong single-use password for each account in conjunction with a password management app. The password managing director lets you lot shop your other passwords in a repository. Then you can use a single, ridiculously strong password for every site.
2. Creature Force
Next up is the animate being forcefulness attack, whereby an attacker tries every possible character combination. Attempted passwords will match the specifications for the complexity rules, e.k., including one upper-case, one lower-case, decimals of Pi, your pizza club, and then on.
A animate being force attack will also try the about usually used alphanumeric character combinations get-go too. These include the previously listed passwords, likewise every bit 1q2w3e4r5t, zxcvbnm, and qwertyuiop. It can take a very long time to figure out a password using this method, just that depends entirely on countersign complication.
Pros: Theoretically, it will crack whatever password by way of trying every combination.
Cons: Depending on password length and difficulty, it could take an extremely long time. Throw in a few variables like $, &, {, or ], and figuring out the password becomes extremely hard.
Stay prophylactic: Ever use a variable combination of characters, and where possible, introduce extra symbols to increment complexity.
3. Phishing
This isn't strictly a "hack," simply falling prey to a phishing or spear-phishing attempt will usually end badly. General phishing emails send past the billions to all manner of internet users around the globe, and information technology is definitely one of the most popular ways to find out someone'due south countersign.
A phishing e-mail generally works like this:
- Target user receives a spoofed email purporting to be from a major organization or business.
- Spoofed e-mail demands firsthand attention, featuring a link to a website.
- This link really connects to a fake login portal, mocked up to appear exactly the same as the legitimate site.
- The unsuspecting target user enters their login credentials and is either redirected or told to try again.
- User credentials are stolen, sold, or used nefariously (or both).
The daily spam book sent worldwide remains high, accounting for over one-half of all emails sent globally. Furthermore, the book of malicious attachments is high, too, with Kaspersky blocking over 148 meg malicious attachments in 2021. Furthermore, Kaspersky'south Anti-Phishing system blocked an additional 253 million phishing links. Call up, this is but for Kaspersky, so the real number is much college.
Dorsum in 2017, the biggest phishing lure was a fake invoice. However, in 2020, the COVID-19 pandemic provided a new phishing threat. In Apr 2020, non long afterwards many countries went into pandemic lockdown, Google announced it was blocking over 18 1000000 COVID-19 themed malicious spam and phishing emails per day. Huge numbers of these emails apply official regime or health organization branding for legitimacy and catch victims off-baby-sit.
Pros: The user literally easily over their login information, including passwords—relatively high striking rate, easily tailored to specific services or specific people in a spear-phishing attack.
Cons: Spam emails are easily filtered, spam domains blacklisted, and major providers similar Google constantly update protections.
Stay condom: Stay skeptical of emails, and increment your spam filter to its highest setting or, better nonetheless, use a proactive whitelist. Utilise a link checker to define if an email link is legitimate earlier clicking.
Social engineering is substantially phishing in the real world, away from the screen.
A core part of any security audit is gauging what the unabridged workforce understands. For instance, a security company will telephone the business concern they are auditing. The "attacker" tells the person on the telephone they are the new office tech back up team, and they demand the latest countersign for something specific.
An unsuspecting individual may manus over the keys without a break for idea.
The scary affair is how often this works. Social engineering has existed for centuries. Being duplicitous to gain entry to a secure area is a common method of assault and one that is only guarded against with education. This is because the attack won't e'er inquire directly for a countersign. Information technology could be a simulated plumber or electrician asking for entry to a secure edifice, and then on. When someone says they were tricked into revealing their password, it is often the result of social engineering science.
Pros: Skilled social engineers can extract loftier-value information from a range of targets. It tin can be deployed against almost anyone, anywhere. Information technology'due south extremely stealthy.
Cons: A social technology failure can enhance suspicions about an impending attack, and dubiousness as to whether the correct information is procured.
Stay safe: This is a tricky one. A successful social engineering assault will be complete by the time you realize annihilation is incorrect. Pedagogy and security sensation is a cadre mitigation tactic. Avert posting personal information that could be afterwards used against you.
5. Rainbow Table
A rainbow tabular array is ordinarily an offline password assault. For case, an attacker has acquired a list of user names and passwords, but they're encrypted. The encrypted password is hashed. This means it looks completely different from the original password.
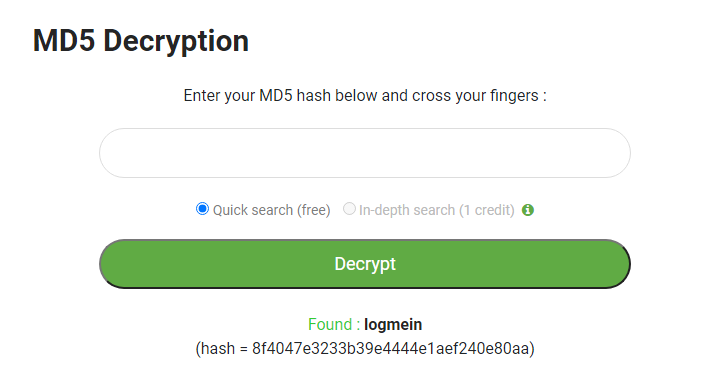
For case, your password is (hopefully non!) logmein. The known MD5 hash for this password is "8f4047e3233b39e4444e1aef240e80aa."
Gibberish to you and I. Simply in certain cases, the attacker volition run a list of plaintext passwords through a hashing algorithm, comparing the results confronting an encrypted password file. In other cases, the encryption algorithm is vulnerable, and virtually passwords are already cracked, like MD5 (hence why we know the specific hash for "logmein."
This is where the rainbow table comes into its own. Instead of having to process hundreds of thousands of potential passwords and matching their resulting hash, a rainbow tabular array is a huge prepare of precomputed algorithm-specific hash values. Using a rainbow table drastically decreases the time information technology takes to crack a hashed password—just it isn't perfect. Hackers tin can buy prefilled rainbow tables populated with millions of potential combinations.
Pros: Can effigy out complex passwords in a short amount of time; grants the hacker a lot of ability over certain security scenarios.
Cons: Requires a huge amount of space to shop the enormous (sometimes terabytes) rainbow table. Besides, attackers are express to the values independent in the tabular array (otherwise, they must add some other entire table).
Stay safe: Another tricky one. Rainbow tables offer a wide range of attacking potential. Avoid any sites that apply SHA1 or MD5 as their password hashing algorithm. Avert whatsoever sites that limit yous to short passwords or restrict the characters you tin can use. Always use a complex countersign.
vi. Malware/Keylogger
Another sure manner to lose your login credentials is to fall foul of malware. Malware is everywhere, with the potential to do massive damage. If the malware variant features a keylogger, y'all could observe all of your accounts compromised.
Alternatively, the malware could specifically target private information or introduce a remote access Trojan to steal your credentials.
Pros: Thousands of malware variants, many customizable, with several easy commitment methods. A expert take a chance a loftier number of targets volition succumb to at least one variant. It tin go undetected, allowing further harvesting of private information and login credentials.
Cons: Risk that the malware won't work, or is quarantined before accessing data; no guarantee that information is useful.
Stay safe: Install and regularly update your antivirus and antimalware software. Advisedly consider your download sources. Do not click through installation packages containing bundleware and more. Steer clear of nefarious sites (easier said than done). Apply script blocking tools to stop malicious scripts.
7. Spidering
Spidering ties into the dictionary assault. If a hacker targets a specific institution or business, they might try a series of passwords relating to the business itself. The hacker could read and collate a series of related terms—or apply a search spider to do the piece of work for them.
You might have heard the term "spider" earlier. These search spiders are extremely similar to those that crawl through the cyberspace, indexing content for search engines. The custom give-and-take list is and so used confronting user accounts in the hope of finding a match.
Pros: Tin potentially unlock accounts for high-ranking individuals within an organization. Relatively piece of cake to put together and adds an extra dimension to a lexicon attack.
Cons: Could finish up fruitless if organizational network security is well configured.
Stay safety: Over again, only apply stiff, single-use passwords comprised of random strings; nothing linking to your persona, concern, organisation, and so on.
viii. Shoulder Surfing
The final option is one of the most basic. What if someone just looks over your shoulder while y'all're typing in your password?
Shoulder surfing sounds a little ridiculous, but it does happen. If y'all're working in a busy downtown café and not paying attending to your surround, someone could become close enough to note your password as yous type.
Pros: Low engineering science approach to stealing a password.
Cons: Must identify the target before figuring out the password; could reveal themselves in the process of stealing.
Stay rubber: Remain observant of those effectually you lot when typing your password. Cover your keyboard and obscure your keys during input.
Ever Use a Strong, Unique, Unmarried-Utilize Password
And so, how exercise you end a hacker from stealing your password? The actually short answer is that yous cannot truly be 100 percent prophylactic. The tools hackers use to steal your data are irresolute all the fourth dimension and in that location are countless videos and tutorials on guessing passwords or learning how to hack a password.
One affair is for sure: using a strong, unique, single-use countersign never injure anyone.
Most The Author
Source: https://www.makeuseof.com/tag/5-common-tactics-hack-passwords/

0 Response to "Id Try This Old Trick Again"
Post a Comment